AI has propelled the digital world forward by optimizing workflows and increasing productivity, but access to new technologies has also improved the work of cybercriminals. In a recent ICS2 webinar, they found that AI was being utilized to make more convincing phishing scams by addressing common issues like grammar and spelling mistakes. Even though the difficulty of recognizing scam emails is becoming less intuitive, the cybercriminal playbook remains the same. Their target is still employees and executives alike, using fraudulent messages to gain access to confidential information, financial details, and even company networks.
Here’s a guide to help business professionals identify phishing attempts and avoid falling victim to them.
1. Analyze the Sender’s Email Address
Phishing emails often appear to come from legitimate companies, but a closer inspection of the sender’s email address can reveal discrepancies. Cybercriminals frequently use slightly altered versions of a company’s domain to fool recipients, such as replacing letters with numbers or adding subtle variations.
What to Look For:
- Misspelled domain names or extra characters (e.g., “admin@micr0soft.com” instead of “admin@microsoft.com”).
- Unfamiliar domain extensions that don’t match the official company website.
When receiving an unexpected email, particularly one asking for sensitive information, always check the full email address—not just the sender’s name.
2. Be Cautious of Urgent Requests
Phishing emails often use urgency to push professionals into quick, unconsidered actions. These messages may claim your account has been compromised, a payment has failed, or a crucial business decision needs your immediate attention. This tactic preys on the fast-paced nature of business professionals, especially in high-pressure environments.
Common Scare Tactics:
- “Your account has been suspended due to suspicious activity.”
- “Payment failure – update your information immediately to avoid service interruption.”
- “Urgent Action needs to be taken”
Legitimate companies rarely demand immediate action via email, especially for sensitive matters. Always take a moment to verify the situation with the appropriate department or vendor before responding.
One example of the many phishing attempts from our interns email!
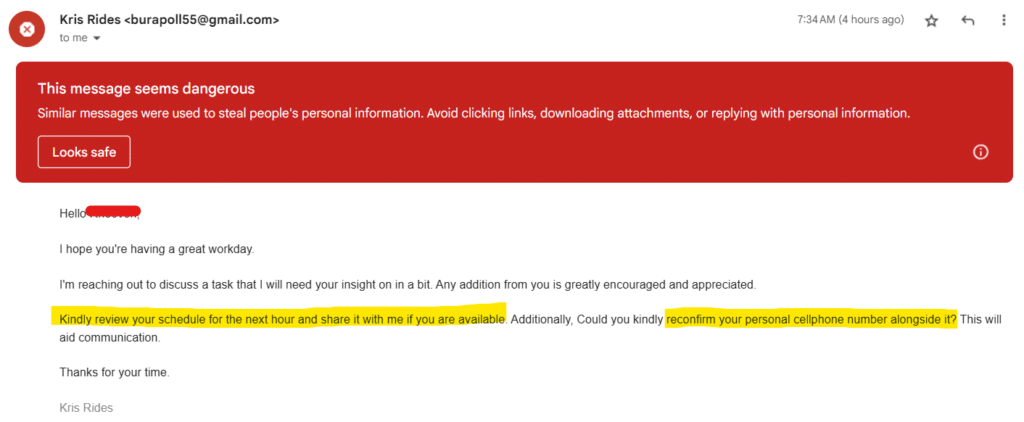
3. Generic Greetings
In business communication, emails are typically personalized. If you receive an email from what appears to be a trusted company but it begins with a vague salutation like “Dear Customer” or “Hello,” it’s a strong indicator of a phishing attempt.
Examples of Red Flags:
- “Dear Valued Customer,”
- “Hello User,”
Professionals should be especially wary when receiving generic greetings from companies or individuals they usually interact with by name. Legitimate business communications are almost always personalized.
4. Examine for Grammar and Spelling Mistakes
While phishing attempts are becoming more sophisticated, many can still contain errors in grammar or spelling. Professional companies take great care to ensure their communication is polished, so any unusual wording, awkward phrasing, or blatant mistakes should raise concerns.
Examples of Mistakes:
- “We detected suspicous login attemp. Please verfy your account now.”
- “To ensure your acount security, click the link below.”
Even minor errors are a warning sign when dealing with emails claiming to be from major organizations.
5. Be Wary of Suspicious Links or Attachments
Phishing emails often include links or attachments designed to compromise your credentials or infect your system with malware. As a best practice, never click on a link or download an attachment unless you are confident it’s legitimate. Hover your cursor over any links before clicking to inspect the URL and ensure it directs you to a legitimate, secure site.
Warning Signs:
- Long, complex URLs filled with random characters, or URLs that don’t match the company’s official domain.
- Unexpected attachments, especially from unknown senders or when no context has been provided.
For professionals handling sensitive company data, clicking a malicious link could result in significant security breaches or financial loss. Always verify the link’s authenticity before engaging with it.
6. Requests for Confidential Information
Legitimate businesses, especially financial institutions, will never request sensitive information such as login credentials, account numbers, or personal identification over email. If an email is asking for such information, it’s almost certainly a phishing attempt.
Examples of Suspicious Requests:
- Asking for your login credentials to reset an account.
- Requesting sensitive personal or company data.
- Asking for immediate payment or billing information.
Always verify requests for sensitive information through direct, secure communication channels with the company or person in question. Never respond directly to the email with such information.
7. Unfamiliar Tone or Context
Phishing emails may contain unfamiliar language, reference services or transactions you don’t recognize, or simply seem out of place. If you receive a communication that doesn’t align with your business dealings or previous exchanges, it’s worth taking a second look.
Examples of Inconsistencies:
- An email referencing a service you haven’t subscribed to.
- Sudden account changes or promotions that seem too good to be true.
- Tone or language that doesn’t match previous communications from the same sender.
Phishing emails can be highly convincing, but they often fall short in replicating the tone, context, or professionalism of genuine business correspondence.
8. Missing or Inconsistent Contact Information
Legitimate business emails usually include full contact details, such as phone numbers, email addresses, and professional signatures. Phishing emails, however, often lack this kind of specificity or use vague, generic contact details.
Warning Signs:
- Lack of full contact details or an official company signature.
- Inconsistent or low-quality branding and logos.
- Contact details that don’t match the official company website.
Before acting on any email that feels suspicious, it’s a good idea to compare the contact information provided with the company’s official website or directory.

What Business Professionals Can Do to Protect Themselves
If you suspect an email may be a phishing attempt, take the following steps:
- Don’t click on any links or download attachments.
- Verify the legitimacy of the email by contacting the sender through official channels. Use a verified phone number or company website rather than responding to the email.
- Report phishing emails to your IT or cybersecurity team to prevent potential damage to your organization.
- Delete the email once you’ve determined it is a phishing attempt to avoid any future interaction.
Lastly a helpful graphic developed by CrowdStrike, helps professionals visually learn the Anatomy of a Phishing Email. Take the time to identify the highlighted points they’ve made, so you can better prepare yourself when these malicious acts land in your email.
Conclusion
Lastly, before responding to suspicious email that seems to check all the boxes that were covered above, leave it for a day or two. Inboxes like Gmail, could take a full day before marking malicious emails as spam. As an added bonus, most phishing attempts do not run a follow-up email on “urgent” activities, so that gives your grace that your attention was not required. For persistent scammers, follow a more direct channel of assistance to the official business website or phone number.
Phishing attacks are a growing threat in the business world, targeting professionals at every level of an organization. Recognizing the signs of phishing emails—such as suspicious email addresses, urgency, poor grammar, and requests for sensitive information—can help protect both you and your company from significant risks. Stay vigilant, verify before you click, and always veer on the side of caution when handling unexpected emails.
If you need assistance in training staff to defend against digital threats, then consult with Kris Rides at kris.rides@tirosec.com and start protecting your data today!
